You’ve likely heard of the ‘Nigerian Prince’ scam, but are you aware of these 4 kinds of social engineering scams and how to prevent them?

If you’ve not heard of the ‘Nigerian Prince’ scam, it’s a form of ‘Phishing‘. If you check your email’s junk folders right now you might see an email with the subject line “Hello!”, “Greetings from your friend!”, “I need help!” or something similar. If you were to open this email, which we don’t recommend, you might see an email body explaining how the writer is locked out of a large sum of money and needs a quick loan from a kind stranger to access it. The loan is usually to pay off some fee or delivery, and once it’s paid off, the kind stranger will receive a portion of this large sum of money.
Once you’ve sent off the money, you’ll either be asked for more money or you’ll never hear from the writer again.
The guiding rule of thumb for guarding against social engineering scams is to always be sceptical of any promises made online – and remember, if it sounds too good to be true, it probably is.
What is Social Engineering?
Simply put, social engineering is a method by scammers to gain access to your personal information, typically by deception. It’s called social engineering because there’s generally either a line of communication involved in which the mark and the scammer will talk to each other. Sometimes, there may not be a communication line involved, but there will be some psychological tricks involved in order to get the mark’s information.
Social Engineering in a Business Environment
If you run or manage a business with multiple employees, it’s not just enough for you to understand cyber security, your employees do and they follow proper procedure when dealing with suspicious calls, messages, or emails.
It’s on each individual employee to protect your business, which is why you need to ensure you have a proper digital culture, and that your employees understand why they can and can’t do certain things.
If you’re a Start Digital member and are concerned about your digital culture or just need some extra help, you can call us in the UK from 9:30am to 5pm on 0151 245 6028. Alternatively, you can email us at support@start-digital.co.uk.
Scareware – The ‘Trusted’ Technician
And Their Main Methods
This scam is initiated in various forms, but most commonly you’ll visit a scareware website that will display a popup at you claiming you have a virus or some other issue and need to call a support line. You may also receive an email or phone call, but the scammer’s initial goal is to get you on the phone.
While on the phone, the scammer will try to scare you and they may sound authoritative, but will likely be persistent to the point of sounding almost desperate. They’ll ask that you download either screen-sharing software or a remote access application.
Once you’ve installed their software, they’ll attempt to ‘wow’ you with very basic commands that anyone can do on their computer.
If you open the command prompt by pressing the ‘Windows Key’ + R and then typing in ‘CMD’. If you were to type ‘ipconfig’ and press enter into the command prompt, you would be greeted with information about your internet connection. If you were a complete layman, you wouldn’t know what you were looking at. “Default gateway?” “Media state… disconnected?” A scammer would use this technical data, or data like it, to spin a story to make it look like you have a virus.
If at any point you question the legitimacy of the scammer, they’ll often remind you that it was you that called them. They can’t be scammers if you called them, right? This is something that falls into the ‘engineering’ part of social engineering.
The scammer will use the remote access software to run scripts or download software that actually are viruses. They will then close down any internet browser window popups that exclaimed you had a virus and congratulate you on your freshly cleaned system. Great job, you did the right thing!
Except… There are a few things the scammers could have done. Let’s talk about the most likely three.
They Might install a Keylogger.
What is a keylogger? A keylogger is a piece of malicious software that runs in the background of your computer and tries to disguise or hide itself so that you don’t know it’s there. A keylogger records the keys you press on your keyboard – some even record your mouse activity and where on the screen you’ve clicked. This information is then sent back to the scammer or hacker. If you’re entering passwords and usernames regularly, the scammer will now have access to those accounts as they’ve been watching you type in your passwords and account information.
How to protect against keyloggers.
Protecting keyloggers is relatively simple if you follow the standard anti-virus protection basics:
- Don’t install suspicious software.
- Run regular virus scans.
- Keep your security firewall up to date.
- Use two-factor authentication on as many accounts as you can.
If you have employees or have other people using servers that you own or manage, you’ll also want to create a usage policy. A usage policy is sometimes necessary for insurance purposes but mainly protects against misuse of your digital property. Without the proper digital policy, you may not even be able to discipline your employees for digital malpractice.
What Should you Do If You’re Concerned You Have a Virus?
If you’re concerned about viruses or suspicious that you may have a virus, downloading trusted anti-virus software like Malwarebytes or Kaspersky and running a full scan is all you need to do to know whether or not your system has any malware. Keep in mind, depending on a few factors like how many files on your system and how old it is, this may take several hours or it may take a few minutes.
They’ll Sign Into your Accounts.
Another common tactic is to hide what they’re doing whilst on your computer. Essentially, they blank out your screen so you can’t see anything while ‘their super software cleans your computer’. The scammers will then route through your computer and look for saved passwords in your browser to log into your accounts and steal your data.
They’ll Ask For Money
This method certainly isn’t as sophisticated as the other two, but the chances are that they’ll ask for money regardless of what they do. Typically, scammers will ask for money in a way that they can’t be tracked I.E. Gift Cards. If anybody ever asks for payment in gift cards, they’re likely scamming you. Even if they aren’t scamming you, they’re likely doing extremely shady things as those gift cards are sold over the internet in a form of modern-era money laundering.
Spoofing Emails & Cyber Infiltration
A spoofed email address is an email address disguised as another email address. This is a rather strong tool in the social engineering toolkit as it can be so simple to do. There are a number of ways to spoof an email address.
- By using email spoofing software.
- Using foreign characters to replace standard Latin characters.
- Using a similar, but misspelt email address.
How to Protect Against Spoofed Emails
Domain Linked Email Address
One way to help prevent someone hijacking your likeness through email is to purchase a domain name and create email addresses from it. For example, instead of ‘name.start-digital@gmail.co.uk’, using ‘name@start-digital.co.uk’. Spoofing a domain name is rather easy for a scammer who knows what they’re doing, but as well as looking professional, it’s an extra barrier to help protect your customers.
Owning a domain-linked email address tells your clients, customers (and your employees!) that you are part of the organisation and are verified to use the domain name. It would be incredibly easy for someone to claim to be a new hire for a company and message people with your company’s name if all they need to do is create a google mail account and add your company name to the front.
Domain names typically cost between £10 – £18. You can purchase a domain name from a variety of domain registrars. To do so, simply search for the domain on their website and continue through the checkout process. For ease of use, we recommend Google, Godaddy, or NameCheap.
Strong Anti-Spam Filters
Some anti-spam filters are able to detect spoofed emails and can send them straight into your junk mail. The accuracy of the filters is largely determined by the email provider itself, and there’s no guarantee it will block all spoofed emails but it definitely will help.
Most well-known email providers (Outlook, Gmail, iCloud, etc) will have strong anti-spam filters enabled by default. Unless you already know what you’re doing, we would recommend not touching these filters.
If you find you’re getting a lot of spam emails to your main folder, we’d suggest changing your email to a provider with better filters.
Keeping a Sharp Eye
It’s the oldest trick in the book. You don’t need to be technically minded to stay safe online, just like you don’t need a bodyguard to stay safe when you’re out and about. You just need to be smart.
If you receive an email that you’re not explicitly expecting, especially if it regards money or sensitive information, double-check the email address. You might find that an ‘l’ has been replaced by a capital ‘i’. You might see a mis-spelling that looks correct at a glance.
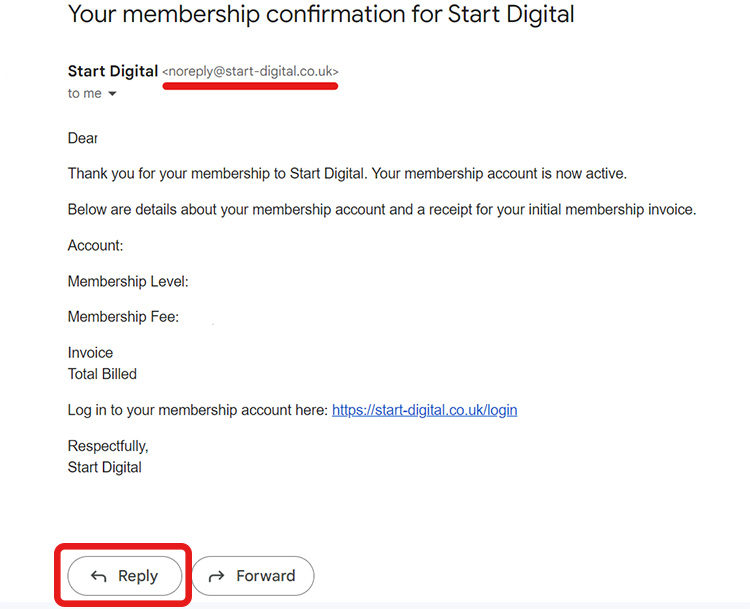
How to Detect Email Spoofing (With Images)
It’s actually very simple to detect a spoofed email. Hitting the ‘Reply’ button and looking at the email address will show you exactly who you’re replying to.
Start-Digital actually spoofs some emails, though with good intentions. When we sent out information about your account, certain emails use the “noreply@start-digital.co.uk” email, but if you were to reply to this, you’d see it actually leads to “info@start-digital.co.uk”.
We spoof this email to let people know it’s automated and doesn’t require a response, but if someone does happen to send us something urgent, we can always respond promptly.
Spear Phishing
Spear phishing is a specific kind of phishing – actually, it’s phishing that targets a particular individual (or company). Spear phishing is generally done with the intent to gather customer data to sell it. Another example of spear phishing is the story of J&R where scammers stole £10,000 directly from the company’s accounts simply by stalking the owner on linked in and sending spoofed emails at certain times.
The Difference between Spear Phishing and Standard Phishing
The actual methods of spear phishing are very similar to that of standard phishing, except any correspondence to the mark will be more personalised.
The biggest change is the research put into the target by the scammer. This is generally done through pretexting and social media, especially LinkedIn. Scammers will scour social media and follow people they think might make a good target. They’ll wait for the perfect opportunity and then strike.
The ‘perfect opportunity may be a holiday, the day of a business deal, or some other important event in which the victim may be distracted.
Pretexting
Pretexting is where a scammer invents a scenario and asks you to prove your identity in order to steal your personal information.
For example, someone calls you up and informs you that they’re part of the fraud department and you may be at risk – but before they can help you, you’ll need to provide your:
- Full name.
- Date of Birth.
- Home Address.
- Alternative Phone Number.
- Years at current address.
- Occupational information.
Some scammers will ask for different information depending on their needs.
Preventing Pretexting Scams
There’s a common theme with all social engineering scams – if you’re not expecting it, you should be suspicious. If someone calls you up and asks for personal information, ask them for their name and their company (if it’s a British company, ask for their company number). If they refuse to give you this information after asking just once, the call is likely illegitimate and you should hang up. If get their name and company information, inform them that you will call back. Any pushback or resistance to you hanging up is a red flag as a scammer understands that once you’ve hung up, you’re gone.
Search online for the company and try to be thorough in checking its legitimacy. If the company is legitimate, you can call them back.
HMRC & Pretexting Scams
It’s unlikely that HMRC would ever ask you for details if they were to call you. Instead, they would likely explain to you how to do things.
For example, if you ever received a call about tax relief evaluations, you would have been invited to set up an interview at a later date. There would be no discussion of your specific account, personal, or business details during the original phone call.
You can find a full list of reasons HMRC will call you here.
General Advice for Avoiding Social Engineering Scams
To avoid falling victim to social engineering scams, remember:
- Don’t trust an organisation that contacts you first and asks for your details.
- If it sounds too good to be true, it probably is.
- If you’re concerned your computer may be infected, download trusted anti-virus software and run a scan.
- Create proper policies and procedures in your business.
- Follow the best practices outlined in our Health Checks & Tool Kits.
If you have any issues with your cyber security, please call in the UK from 9:30am to 5pm on 0151 245 6028. Alternatively, you can email us at support@start-digital.co.uk.
If you’re looking to protect your business and form a proper digital culture, you can sign up for a membership today on our sign up page.